How to implement Multi-Factor Authentication (MFA) in Hospitals and Medical Institutions?
International System Research Co., Ltd.
Published: March 17, 2025
Guidelines for the Secure Management of Medical Information Systems
In May 2023, the Ministry of Health, Labour and Welfare formulated the "Guidelines for the Secure Management of Medical Information Systems, Version 6.0, System Operation Edition". The guidelines include the following provisions regarding authentication and ID management:
Medical information systems must have functions to identify and authenticate users.
Means for identifying and authenticating all staff and related personnel accessing medical information systems must be provided and managed uniformly within medical institutions.
When using passwords for authentication, systems adopting two-factor authentication or equivalent measures must be introduced during new implementation or updates (targeting medical information systems expected to be operational by fiscal year 2027).
Procedures must be established for managing IDs used in medical information systems, including maintaining registers, conducting regular inventories, and deleting unnecessary IDs as appropriate.
In essence, it will be required to establish a system where authentication is always performed when accessing medical information systems, along with implementing two-factor authentication and regular ID management.
The Ministry of Health, Labour and Welfare stated the purpose of this revision as follows:
For health insurance medical institutions and pharmacies, the introduction of online qualification verification has been mandatory in principle since April 2023. Moving forward, network-related security measures described in the guidelines will be commonly required for more medical institutions. Furthermore, given the increasing diversification and sophistication of cyberattacks against the medical field and medical information systems, which have a significant impact on medical institutions' clinical operations, the content has been reviewed, focusing on the security management measures required of medical institutions.
Ministry of Health, Labour and Welfare: Guidelines for the Secure Management of Medical Information Systems, Version 6.0 (May 2023)"
With the introduction of online eligibility verification with the launch of the My Number Health Insurance Card, it is now possible to access the online eligibility verification system and view medical treatment/drug information, etc. Furthermore, the "emergency medical information viewing function" was launched in December 2024, which allows patients to view medical information, etc. by verifying their identity using their My Number Health Insurance Card even in emergencies when it is difficult to obtain their consent.
The online qualification verification system falls under "medical information systems" in the aforementioned guidelines, thus requiring two-factor authentication for login.
(Reference: Ministry of Health, Labour and Welfare "Preparatory Work Manual for the Introduction of Emergency Medical Information Viewing Function, October 2024, Version 1.2")
Healthcare Cyberattack Trends: Key Similarities & How to Prepare
As one of the aims of the revised guidelines, there has been a sharp increase in cyber attacks using ransomware in recent years, and medical institutions are no exception, suffering from many of the damage they have suffered. When we look at these cases, we can see that there are several commonalities.
- VPNs set up for vendor remote maintenance were the intrusion point.
- VPN vulnerabilities were left unpatched.
- Authentication relied on IDs/passwords, with common use of easily guessed or reused passwords.
- Administrator privileges were granted to general users.
- Antivirus software was disabled due to considerations for other systems or changes made by attackers.
As a result of ransomware attacks, medical institutions have suffered severe consequences, such as being unable to access electronic medical records due to encryption or system failures, leading to manual record-keeping or restricting medical operations for several months.
What is MFA and why should you use it?
Across industries worldwide, from finance to healthcare, Two-Factor Authentication (2FA) and Multi-Factor Authentication (MFA) are rapidly becoming a mandatory security standard. This isn't just a recommendation; it's a critical shift in how organizations protect sensitive data and user access. What's behind this widespread, urgent embrace of enhanced authentication protocols?
Problems with Passwords
While passwords are a common authentication method, they pose various problems and risks.
Security Challenges
Easy Impersonation
Anyone who knows an ID and password can easily impersonate a legitimate user to access and log in to a system. The system will then mistakenly identify them as a legitimate user, delaying the detection of unauthorized access.
Low Phishing Resistance
Since both the user and the server hold passwords, and identity verification is performed by exchanging passwords over a network, there is a risk of them being intercepted by a third party midway.
Usability Challenges
Difficulty in Creating and Remembering Complex Passwords
To enhance security, it's necessary to create hard-to-guess passwords and set different passwords for each service. However, due to difficulty in remembering them, this often leads to the use of simple passwords or password reuse.
Difficult Account Management for Administrators
When using multiple services, administrators must manage account settings and password policies tailored to each service. Additionally, password reset requests from users add significant administrative burden and effort.
Multi-Factor Authentication (MFA): An Overview
One way to solve these problems is with MFA. Even if one piece of information is compromised, setting up multiple information requirements can reduce the risk of unauthorized access.
Three Factors of Authentication
The term "factor" used in two-factor authentication and multi-factor authentication refers to three types: knowledge, possession, and biometrics. These are known as the "three factors of authentication."
• Knowledge Factor: Information that only the individual knows, such as a password or security question.
• Possession Factor: Information that only the individual possesses, such as a security key or smartphone.
• Biometric Factor: Unique biological information or characteristics, such as fingerprints or facial features.
A method of authentication that uses two or more of the three factors mentioned above is called "two-factor authentication" or "multi-factor authentication."

Weaknesses of OTP (One-Time Password)
One method of MFA involves using a password plus an OTP. Since the OTP is generated on an app on a different device (smartphone) than the login device, this constitutes MFA using a knowledge factor (password) and a possession factor (smartphone). However, both passwords and OTPs are entered on the web and sent to the server via the network, offering no resistance to real-time phishing. Since stacking factors with no phishing resistance does not enhance overall resistance, the security strength is arguably insufficient.

The primary reason for recommending MFA adoption is, of course, enhanced security. However, it also leads to improved convenience by reducing the burden on in-hospital system users and administrators, which was a drawback of password authentication.
3 Key Points for Implementing MFA
The phrase "implementing MFA" can raise questions about where to start or how to proceed. If you're juggling multiple responsibilities, you might even think, "I simply don't have much time or effort to spare." Here are three key points to consider for MFA implementation.
Centralized Account Management with Single Sign-On (SSO)
If your hospital uses multiple services, each may require a separate ID/password, leading to cumbersome login procedures. Utilizing an SSO service can centralize authentication entry points and allow for single-point management of authentication method settings.
Ensuring Secure Devices with Access Restrictions via Device Certificates
A PC with a device certificate installed is considered a "possession factor," allowing you to achieve MFA with minimal burden, without needing to purchase new authenticators or replace devices with biometric features.
Learn more about Device CertificatesSelecting Authentication Methods Suited for On-site Operations and Achieving Strong MFA with Passkeys
Passkeys (FIDO authentication credentials) are gaining attention as a phishing-resistant MFA method that can replace passwords. While FIDO-compliant authenticators are required for passkey authentication, various authenticators are currently supported, so choose one that fits your actual operating environment.
Examples of Authenticators Supporting Passkeys (FIDO Authentication Credentials)
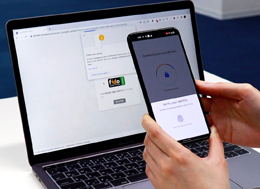
Authentication via Smartphone
This method uses the fingerprint or facial recognition features on a smartphone, separate from the device you wish to log in to, as an authenticator. If you always carry your smartphone, authentication is simple, similar to unlocking your device, by simply placing your finger or face on the sensor.
However, potential drawbacks include the need to carry a separate authentication device and the inconvenience of removing masks or gloves for each authentication if worn.

Authentication via PC-Integrated Biometric Features
Many general PCs on the market today come equipped with biometric authentication features. Prominent examples include Windows Hello and Touch ID/Face ID, which can be used for authenticating logins to services.

Authentication via Security Key
FIDO2-compliant security keys offer strong, phishing-resistant authentication. They are small and lightweight, available in various forms such as those that can be attached to a neck strap or key case, or even bracelet types. A prominent example is the YubiKey, provided by Swedish-based Yubico.
Learn more about Security KeysLearn more about YubiKeyMulti-Factor Authentication (MFA) Usage Examples in Medical Settings
The following are examples of SSO and MFA operations envisioned for actual medical institutions:

Shared Devices Used by Multiple Staff
By routing through an SSO service, even with the same login screen, users are identified and verified via ID and MFA, displaying a cloud environment tailored to each user. Only pre-configured accessible services are shown, preventing situations where unauthorized individuals might access services they shouldn't.

Email Service
If an email service is subjected to unauthorized access, there is a risk of email addresses, names of correspondents, information in the body of emails, and attached data being viewed or stolen. By implementing MFA for login instead of password authentication, which makes impersonation easy for third parties, security is enhanced.
Furthermore, even if your current email service does not support MFA, you can configure MFA settings if integration with an SSO service is possible.

Tablets
With the adoption of electronic medical records and the digitalization of image data such as X-rays, more medical institutions are using tablets. Since tablets are more portable than PCs, they are often used for rounds and other mobile tasks, meaning they are handled by many people. While many devices support fingerprint and facial authentication, removing gloves or masks for each login can be inconvenient. To avoid issues with account creation and deletion procedures due to staff changes, we recommend MFA with security keys.

Google Cloud and YubiKey Integration
The wave of DX (Digital Transformation) is also reaching medical institutions, and the transition to cloud services like Google Cloud will continue to advance. Google and Yubico have formed a partnership, making the use of YubiKey for logging into Google Cloud a highly effective combination.
Read Adapta's YubiKey Success Story, a Medical IT Service Provider that achieved both fast and secure loginSteps to Implement SSO Service for MFA Realization
The first step is to understand your current situation. While referencing the guidelines introduced earlier, identify any security shortcomings and inventory existing devices and systems. Based on current challenges and device usage, compare and consider which MFA approach to adopt before moving to the implementation phase.
If a system supports MFA, configure MFA as the login method and register the authenticator. If the system does not support MFA, or if you use multiple systems, you can implement an SSO service to centralize authentication and then apply MFA. (Even if your current systems, including electronic medical record systems, are not explicitly listed among the SSO-compatible services, integration may still be possible. We can also verify compatibility, so please feel free to consult us.)
As you proceed with MFA setup, equally important is communicating with users (employees). Explain the benefits, including improved convenience, and provide training on the authenticators and authentication methods required for login.


In some medical institutions, IT and system responsibilities may be shared with other duties, rather than being handled by a dedicated IT professional. If you are interested in strengthening authentication with MFA and understand its necessity, but feel overwhelmed, please consult with your system implementation or maintenance vendor (external provider) first.
What is CloudGate UNO: The Platform for Unified ID & Access Management, Passwordless Login, and Multi-Factor Authentication (MFA)?
CloudGate UNO is an identity management platform that balances security and convenience with flexible access restrictions and strong authentication. We provide SSO features based on the zero-trust principle, which assumes "never trust, always verify" every access.
Feature 1: Granular Access Restriction per Service
Our approach verifies (authenticates) every access to cloud services, allowing you to set access restrictions not only per user or group but also per cloud service.
Feature 2: Comprehensive Access Restriction Features
To ensure secure sign-on, when accessing cloud services, you can identify and restrict access based on who (Who) is signing on, what (What) device they are using, when (When) they are signing on, where (Where) they are signing on from, and how (How) they are signing on.
Feature 3: Enhanced User Convenience
CloudGate UNO offers rich features to enhance user convenience. Besides eliminating login issues with single sign-on, users can choose their authentication method, enabling operations tailored to their on-site needs.

Ready to Enhance Your Security?
Get more information on how to implement Multi-Factor Authentication (MFA) and Single Sign-On (SSO) in your organization.
Feel free to call us!
03-5942-8314



