Explained by the Official Manufacturer's Distributor

What is YubiKey?
A Comprehensive Guide to Its Benefits and Overview
Feel free to contact us for consultations or inquiries regarding implementation
Contact UsFor immediate assistance, please call us at 03-5942-8314.

YubiKey (Security Key)

What is YubiKey?
YubiKey is one of the "security keys (hardware tokens)" that can be used for multi-factor authentication with a high level of security.
The basic usage of YubiKey is just to insert it into a USB port and touch it. It can be used on various operating systems and does not require special software or drivers. Compatible services are increasing each year, and it is gaining attention as a next-generation security solution.
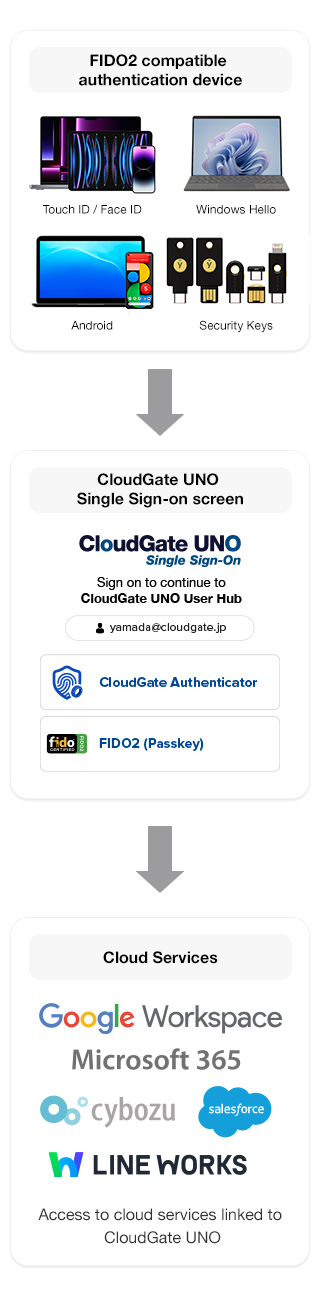
YubiKey, manufactured by Yubico, a US-based company based in Sweden, supports the latest authentication protocols such as FIDO2 as well as traditional protocols such as TOTP, providing strong two-factor authentication, multi-factor authentication, and passwordless authentication with a single touch.
YubiKey is manufactured in the U.S. and Sweden and has sold over 22 million units in more than 160 countries worldwide to companies such as Google, Meta (formerly Facebook), Microsoft, and the U.S. Department of Defense.

Guide Available Here
YubiKey Beginner's Guide (1MB)
What is a Security Key?
A security key is a physical device that enables highly secure, passwordless multi-factor authentication (MFA).
While often a small USB device like a YubiKey, the term also includes other formats like access cards and wristband-style keys.
Why are security keys necessary?
Passwords are a major security risk, with a reported 80% of hacking incidents originating from compromised passwords. To counter this, authentication methods has evolved:
Two-Step Verification (2SV): This method often uses a password plus a "knowledge factor" like a secret question, which is easily compromised and offers minimal security.
Two-Factor Authentication (2FA) / Multi-Factor Authentication (MFA): A common form of 2FA uses a password with a one-time code sent via SMS or email. However, this is also vulnerable to phishing attacks.
Therefore, a security solution that does not use passwords, but instead uses "possession factors (e.g: device)" and "biometric factors (e.g.: fingerprint/facial recognition)", became necessary. Security keys were developed to meet this need.
Learn More About Security KeysLearn More About Passwordless AuthenticationLearn More About Multi-Factor Authentication (MFA)Types of Multi-Factor Authentication (MFA)




Multi-Factor Authentication + Public Key Cryptography
(Passkey)
Combines two or more factors from:
"Possession information" such as devices, which only the user has.
"Knowledge information" such as PINs.
"Biometric information" such as face or fingerprints.

Two-Factor Authentication (2FA)
Password + One-Time Password via app or SMS

Two-Step Verification
Password + Secret question, etc.
Weaknesses of Two-Step Verification
Two-step verification is a method that performs authentication in two separate steps, regardless of which factors are used. This means that authentication can be completed even with a single factor. For example, simply entering a password twice can be considered two-step verification, so it does not necessarily provide a high level of security.

Weaknesses of Non-FIDO2 Multi-Factor Authentication (Two-Factor)
In the case of multi-factor authentication (MFA) that uses SMS notifications or one-time password (OTP) apps, the security is slightly higher compared to the two-step verification that uses only "knowledge factors." This is because it confirms "possession factors" in addition to "knowledge factors." However, its resistance to phishing remains low. If an attacker prepares a fake website, it is not difficult to trick a victim into entering both their password and the one-time password.
Strengths of Passkeys & Security Keys
Authentication with a passkey, including a security key, uses a pre-registered physical authenticator for multi-factor authentication (MFA).
Its core strength lies in public-key cryptography: a unique private key is stored securely on the device and is never transmitted over the network. The authenticator simply signs a unique server challenge, which is verified by a corresponding public key. This prevents the private key from being exposed on the network. The signed challenge cannot be reused, and tampering with authentication information is difficult, giving it strong resistance against man-in-the-middle attacks.
This cryptographic process makes passkeys and security keys virtually immune to phishing as a remote attacker cannot steal the private key. Devices like the YubiKey are a leading example, supporting the FIDO2 standard to enable strong, passwordless authentication with a simple touch.
Learn More About FIDO2

Feel free to contact us for consultations or inquiries regarding implementation
Contact UsBenefits of Security Keys (in the case of YubiKey)
As mentioned, there are various authentication methods for multi-factor authentication that meet FIDO2, besides security keys.
The reasons for choosing a security key are as follows:

High-Level and Flexible Security Enhancement
High Security with FIDO2 Compliance
Compliant with the industry's latest and highest-level FIDO2 standard,
reducing security risks.
Start Security Improvement from Specific Departments
Supports enhanced security for research institutes and departments handling confidential or personal information.
Unify Login Strength Across the Company
Ideal for strengthening authentication for employees who cannot be issued smartphones, such as those at subsidiaries, partner companies, or temporary staff.
Phishing Resistance
Information exchange is completed entirely between the device and the security key, providing high resistance to phishing.
Compatible with Environments Where Smartphones Cannot Be Used
Authentication can be strengthened in environments where smartphones are restricted, such as call centers or customer on-site locations.
Enhanced Login for Shared Devices
Utilized for strengthening authentication in call centers or stores where multiple people share devices, and for store devices with high employee turnover, such as temporary or part-time staff.

Excellent Hardware Design
Low Risk of Security Breach Even if Lost
Possesses high tamper resistance, resulting in low security risk from reverse engineering even if lost.
Low Unit Cost
Lower unit cost compared to other authentication devices like smartphones that also support FIDO2 authentication.
Supports Various Interfaces
YubiKey supports USB Type-A, USB Type-C, NFC, and Apple Lightning.
Durability and Water Resistance
YubiKey is impact-resistant and less prone to failure even when submerged in water, making it ideal for industrial sites such as factories.
No Replacement Needed Due to Battery Depletion
Replacement due to degradation is almost unnecessary for several years.
Secure and Wide Range of Use
The key is treated like a keyboard or mouse and is not recognized as a memory region. For example, even if a PC or smartphone device breaks down, work can continue on a different device.
Integration with SSO (Single Sign-On) Services
Security keys, when integrated with SSO services, make authentication stronger and more convenient. By performing multi-factor authentication using YubiKey in addition to a password, the risks of phishing attacks, credential stuffing, and account hijacking are reduced, achieving strong end-to-end security from the user to the service. Furthermore, users benefit from reduced password management hassle and eliminated time loss due to account lockouts from login errors.
Our SSO service, "CloudGate UNO," supports security keys, and we also assist with company-wide deployments for our clients.
What is Single Sign-On (SSO) Authentication?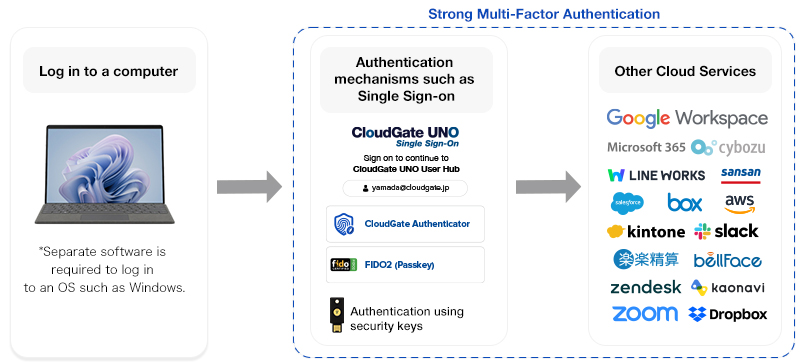

What is Yubico, the manufacturer of YubiKey?
Yubico was founded in Stockholm, Sweden in 2007. Since its inception, it has sold over 22 million YubiKeys in more than 160 countries, making it the largest manufacturer in the security key industry. It was listed on Nasdaq First North Growth Market in Stockholm in 2003. Headquartered in both California, USA and Stockholm, Sweden, Yubico also has manufacturing facilities in both countries. The company is dedicated to developing industry-standard security specifications and played a central role in the creation of the FIDO2 standard.
Differences from Other Security Keys
In addition to Yubico's "YubiKey," other well-known security keys include AuthenTrend's "ATKey.Pro" and Swissbit's "iShield Key."

YubiKey
Manufacturer: Yubico
Headquarters: Sweden/USA
Key Features
- Possession + Knowledge Two-Factor Authentication (PIN entry → touch to use)
- Possession + Biometric (Fingerprint version)
- Highly robust and water-resistant
- Most interfaces supported
- Industry leader

ATKey.Pro
Manufacturer: AuthenTrend
Headquarters: Taiwan
Key Features
- Possession + Biometric Two-Factor Authentication
- Affordable fingerprint authentication
- Small size, not obstructive
- Relatively inexpensive and easy to procure
- Firmware upgrade possible after delivery

iShield Key
Manufacturer: Swissbit
Headquarters: Switzerland
Key Features
- Possession + Knowledge Two-Factor Authentication (PIN entry → touch to use)
- Highest robustness and water resistance
- Relatively inexpensive and easy to procure
All companies comply with FIDO2, meaning there is no difference in security levels. When selecting for enterprise companies, it is necessary to consider procurement methods, track record, and management methods during firmware updates, in addition to device features.

Advantages of Choosing YubiKey
- Pioneer in the field with extensive track record
- Extensive product lineup
- Compliant with U.S. Federal Information Processing Standards (FIPS)
We, ISR, offer "YubiKey as a Service," a YubiKey subscription service that supports reduced initial costs, efficient deployment, and long-term operational assistance.
Learn More About YubiKey as a ServiceYubiKey Usage Scenarios
Our security specialists propose particularly recommended usage scenarios.

Unify the security level for "remote work" and "everyone using a shared PC". Reduce the risk of losing an authenticator and the cost of purchasing an authenticator.
For enterprise companies and call centers attempting to implement multi-factor authentication using smartphones or PCs, significant investment is required, and the financial and security risks associated with device loss or malfunction are high. YubiKey is more affordable than smartphones, and even if lost, the security risk is low. Therefore, it is ideal for strengthening authentication for employees who cannot be issued smartphones, such as those at subsidiaries, partner companies, or temporary staff.
Ideal for mitigating risks in Privileged Access Management (PAM). Quickly update authentication for departments/positions where security updates are difficult
Although administrators and specialized departments in government agencies and financial services need to urgently address security risks, they are limited in the devices they can use and find it difficult to update their authentication processes. YubiKey is easy to implement and supports a variety of interfaces, allowing them to quickly upgrade their authentication processes to the highest level.


Establishing an authentication protocol for areas where smartphone use is restricted
Even in environments with smartphone usage restrictions, such as data centers, industrial plants, and call centers, implementing YubiKey allows for the establishment of FIDO2-compliant authentication protocols.
Furthermore, YubiKey's robust and water-resistant design ensures durability in field work, minimizing downtime due to authenticator failure.
YubiKey Case Study
Hyatt Hotels
The YubiKey implementation story that reduced security risks,
improved operational efficiency, and enhanced customer experience.

YubiKey Case Study
Medical IT Service Provider Adapta
Achieved both rapid login experience and enhanced security for medical professionals with YubiKey.
Read Case Study
YubiKey Product Lineup
YubiKey comes in multiple types, each supporting different security protocols and interfaces.
Since the optimal model varies depending on the usage environment, please consult with us.
 |  |  |  |  |  | |
|---|---|---|---|---|---|---|
| Product Name | YubiKey 5 NFC | YubiKey 5C NFC | YubiKey 5Ci | YubiKey 5C | YubiKey 5 Nano | YubiKey 5C Nano |
| Interface | USB-A | USB-C | USB-C/Lightning | USB-C | USB-A | USB-C |
| NFC Compatible | ||||||
| FIDO2 Compatible | ||||||
| OTP, PIV Compatible |
 |  |  |  | |
|---|---|---|---|---|
| Product Name | Security Key NFC by Yubico | Security Key C NFC by Yubico | YubiKey Bio (FIDO Edition) | YubiKey C Bio (FIDO Edition) |
| Interface | USB-A | USB-C | USB-A | USB-C |
| NFC Compatible | ||||
| FIDO2 Compatible | ||||
| OTP, PIV Compatible |
For YubiKey pricing, please contact us or a reseller.
YubiKey Implementation Hurdles and Solutions
While YubiKey is easy to use, there are some hurdles when deploying it to a large number of users.
Initial Setup Requires Effort
Especially for PIN setup, it is advisable to avoid entrusting this task to a large number of users. If initial setup is done internally, it will require considerable effort.


Contract with a Reseller for Initial Setup Delegation
We offer PIN initial setup delegation services. Not all resellers can delegate initial setup, so please confirm if your YubiKey vendor can provide this service.
Initial Cost
Although more affordable than smartphones, the initial cost of purchasing devices can be a hurdle.


Subscription-based Purchase
To reduce initial costs, we recommend starting with a small deployment to a single department or opting for a subscription-based purchase.
We are the sole provider in Japan offering "YubiKey as a Service," a subscription service that minimizes initial costs.
User Training and Resolving Operational Questions
Disseminating operational methods to users unfamiliar with YubiKey requires significant effort and specialized knowledge.


Seek Support from a Specialist
Consider requesting assistance from experienced specialists for questions and orientation. Specialists need not only YubiKey knowledge but also deep knowledge of YubiKey's integration partners, such as SSO. For integration with CloudGate UNO specifically, please contact us.
How to Purchase YubiKey
YubiKey can be acquired through a subscription model or a one-time purchase.

One-time Purchase Through a Reseller
This involves purchasing the necessary YubiKeys as a one-time transaction from a reseller, including us.
A disadvantage of one-time purchases is that resellers may not support firmware updates or changes to different types of YubiKeys after the initial purchase.
We also support YubiKey sales on a one-time purchase basis, so please feel free to contact us.




