What is a Security Key? YubiKey and Titan Explained
International System Research Co., Ltd.
Last Updated: March 3, 2025|Published: February 7, 2025
Why Security Keys Are Needed
IDs and passwords have been the most common authentication method used in various situations. However, they are constantly exposed to risks like leakage and theft, and if they fall into the wrong hands, they can lead to unauthorized access through impersonation.
According to a report published by the Council of Anti-Phishing Japan in June 2024, the number of phishing reports in Japan has been increasing year by year, with the latter half of 2023 showing the highest results to date.
Furthermore, according to "Threats in Cyberspace in 2023" published by the National Police Agency in March 2024, there were 197 reported ransomware incidents in 2023. Approximately 82% of effective responses from victim organizations indicated that intrusions were likely due to vulnerabilities in telework equipment like VPN devices and remote desktops, or the use of weak authentication credentials.
Given this background, it's clear that authentication solely relying on IDs and passwords is no longer sufficient to protect valuable corporate information assets. In this blog post, we'll introduce "Security Key," which enable stronger and more convenient authentication than passwords.
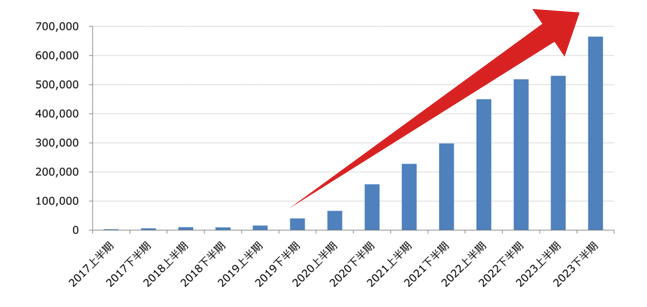
Number of Phishing Reports in Japan
Reference: Phishing Countermeasures Council "Phishing Report 2024"
What is a Security Key?

A Security Key is an external authentication device. It connects to your PC like a USB drive, and authentication is completed simply by touching it with a PIN code or by placing your finger on a fingerprint sensor, allowing users to easily achieve highly secure authentication.
Furthermore, even if a Security Key is lost and falls into unauthorized hands, it's difficult to identify the owner, and without the PIN code or fingerprint, authentication cannot be performed. This significantly reduces security risks compared to password authentication.
Features and Uses of Security Keys
Differences Between Two-Factor (Multi-Factor) Authentication and Two-Step Verification
Authentication using a Security Key is performed using two of the "three factors of authentication"—knowledge, possession, and biometrics—thus qualifying as "two-factor authentication (multi-factor authentication)."
"Possession Factor (having a Security Key)"
"Knowledge Factor (PIN code)"
"Possession Factor (having a Security Key)"
"Biometric Factor (face, fingerprint, etc.)"
There's also the term "two-step verification," which refers to how many steps authentication is divided into, rather than the number of factors used. For instance, simply entering a password (a "knowledge factor") twice would qualify, meaning it may not provide strong authentication depending on the chosen methods.

Security Benefits of Multi-Factor Authentication Using FIDO Authentication (Passkey Authentication)
While there are various types of Security Key, those supporting the FIDO standard are preferable from a security standpoint. FIDO authentication is an authentication technology developed by the FIDO Alliance, an organization aiming to promote passwordless authentication. It is considered highly resistant to phishing.
FIDO authentication uses a public-key cryptography system with a pair of keys—a private key and a public key—to verify identity. The private key is securely stored within the authenticator and cannot be extracted; it can only be used after successful identity verification via biometrics or PIN. The public key is shared with the server.

During authentication, the authenticator uses the private key to sign the authentication request sent from the server and sends it back. The server then uses the corresponding public key to verify the signature and confirm the user's legitimacy. The only action the user performs is the identity verification (fingerprint authentication, PIN entry) to use the private key.
Currently, the FIDO authentication credentials used for authentication are called "passkeys," and an increasing number of companies are adopting passkey authentication as a login method for their services, replacing passwords.
Learn more about Multi-Factor AuthenticationLearn more about Passwordless Authentication with FIDO2Features of FIDO-Enabled Security Keys
Highly Resistant to Phishing
Unlike password authentication, which exchanges the authentication credentials themselves over the network, passkey authentication only sends the authentication result to the server. This eliminates the risk of credentials being intercepted during communication.
Since each authenticator has a unique identifier linked to the service (login destination), authentication requests from phishing sites with different identifiers will be rejected, no matter how sophisticated they are.
Excellent Convenience
Login is completed with simple operations, such as just touching a fingerprint sensor or entering a PIN and then touching the Security Key. This allows users to authenticate without the hassle of setting, remembering, or typing complex passwords.
Being an external device, it can be used with various terminals.
Low Risk of Misuse if Lost
Not only is it difficult to identify the owner from a Security Key, but it also has high tamper resistance, making it difficult to extract stored information. Therefore, even if lost, the risk of misuse is considered low.
It is treated similarly to a mouse or keyboard and is not recognized as a memory area, which also contributes to reducing management burden.

Benefits Beyond Security

Inexpensive and Easy to Manage
Most Security Keys have lower initial deployment costs compared to smartphones or PCs, and it's easy to purchase replacements if lost or damaged. Furthermore, there's no need to consider depreciation, simplifying asset management.

Easy to Carry
Many Security Keys have key chain holes, allowing them to be carried with house keys. Thinner types can also be conveniently placed in an employee ID card holder or wallet.

High Durability
Most Security Keys are resistant to impacts from drops, ensuring that authentication functions are not impaired. They also have a longer operational lifespan than smartphones or PCs.
Use Cases for Security Keys
Security Keys are useful for regular office tasks, but they are also effective for security measures for users who do not have FIDO-compliant authenticators on company-issued devices, or for those who work in environments with shared PCs or mobile phone restrictions, such as call centers, general hospitals, and data centers.

Call Centers
If there are many part-time employees, providing smartphones to everyone for multi-factor authentication via an authentication app might be impractical. Security Keys are low-cost, low-effort, and easily accommodate personnel changes.
Additionally, since each individual has their own external authenticator, they are convenient for environments using shared PCs.

Medical and Nursing Care
It's necessary to log into systems many times a day for tasks like checking records and administrative work. Using Security Keys can reduce login time and effort, allowing more time to be dedicated to treatment and care duties.
Read Case Study
Finance
While stronger security is required, changing authentication processes, such as restricting equipment usage, presents high hurdles. Security Keys are easy to implement and support various interfaces, allowing for rapid enhancement of authentication processes.

Hotels
In front desk operations, where users are constantly visible, OTP authentication requiring smartphone interaction may not create a good impression. Security Keys are small and inconspicuous, allowing authentication to be completed more quickly than OTP authentication.
Read Case Study
Manufacturers
Due to the increase in supply chain attacks, there is a growing demand to unify security levels across related and subcontracted companies. Security Keys are low-cost and support various firmware versions, enabling simultaneous implementation even when companies use different devices.
Additionally, they can be used without restrictions in areas where smartphones are prohibited, such as factories.
Read Case StudyRepresentative Services that Can Use Security Keys

Windows
You can select a Security Key as a sign-in option for Windows Hello.
Also, with certain Security Keys and Windows versions, it's possible to log in to local Windows accounts.

Microsoft 365
Azure
When signing in to your Microsoft account, you can use a Security Key instead of your username and password.

Apple ID
If two-factor authentication is set up for your Apple ID and your device is a compatible version, you can use a Security Key for login.
One of the conditions for use is to prepare and register two security keys, including a backup.

CloudGate UNO
(SSO Service)
With our CloudGate UNO, you can easily set up a Security Key as an authenticator.
Representative Security Keys Supporting FIDO Standard

YubiKey / Yubico
YubiKey supports the latest protocols like FIDO2 as well as traditional authentication protocols such as TOTP, enabling strong two-factor, multi-factor, and passwordless authentication with a single tap. Provided by Yubico, headquartered in the US and Sweden, it has sold millions of units to over 50,000 companies in more than 120 countries worldwide, including Google, Meta (formerly Facebook), Microsoft, and the US Department of Defense.
Learn more about YubiKey
Titan Security Key / Google
This key enables two-factor authentication by serving as the second factor after entering an ID and password. It's recognized as a possession factor when inserted into a device (or tapped against it for NFC) and touched. It incorporates a hardware chip designed by Google.

iShield Key / Swissbit
This key provides two-factor authentication using a possession factor and a knowledge factor (PIN). It is offered by Swissbit, headquartered in Switzerland.
Disadvantages of Security Keys
Security Keys do have some disadvantages.
Risk of Loss
The primary disadvantage is the inability to log in if the key is lost or forgotten. However, this issue can be mitigated by registering alternative authentication methods or by registering and holding a backup Security Key.
Initial Implementation Cost
As a physical device, a significant initial investment is required for purchase.
Other
"Security Keys"
Other "Security Keys"
Besides external authentication devices, the password used for Wi-Fi connections is also referred to as a "network Security Key."
How to Use a Security Key (YubiKey)
So, what's the process for actually using a Security Key? As an example, we'll explain the initial setup and daily authentication for a YubiKey.
Initial Setup
First, you'll register your PIN and/or fingerprint for identity verification. For Windows, the necessary functions for YubiKey registration are built-in. For other operating systems, you can use software provided free by Yubico for setup.
Initial Setup Using a Windows Device

Insert YubiKey into Windows device

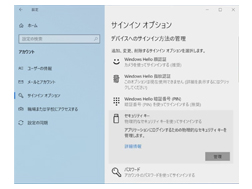
From settings, select "Sign-in options." Click "Manage" under "Security Key."

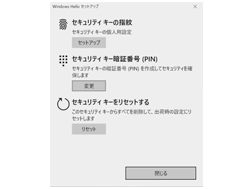
From "Setup," follow the instructions to register your fingerprint and set your PIN.

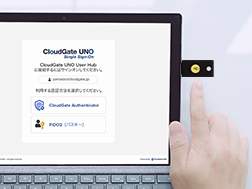
For fingerprint authentication: Touch and lift your finger from the sensor several times. For PIN: Enter the PIN code and touch the sensor.

Daily Authentication
Once the initial setup is complete, you'll register the YubiKey with the service or system you wish to log into using the Security Key. This will make the Security Key appear as an authentication method for future logins.
Using a Security Key with CloudGate UNO: An Overview
【Security Key Registration】
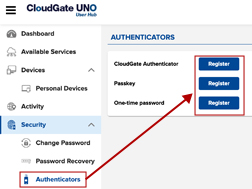
Sign in to CloudGate UNO, click the "Authenticators" tab. Select "Register" for Passkeys.


Enter the desired authenticator name and click "Register."


Insert the Security Key into the device and authenticate using fingerprint or PIN + touch, following the OS instructions.
Note: As this is a FIDO-enabled Security Key, it will be treated as "Passkey Authentication" within CloudGate UNO.
【Authentication with Security Key】
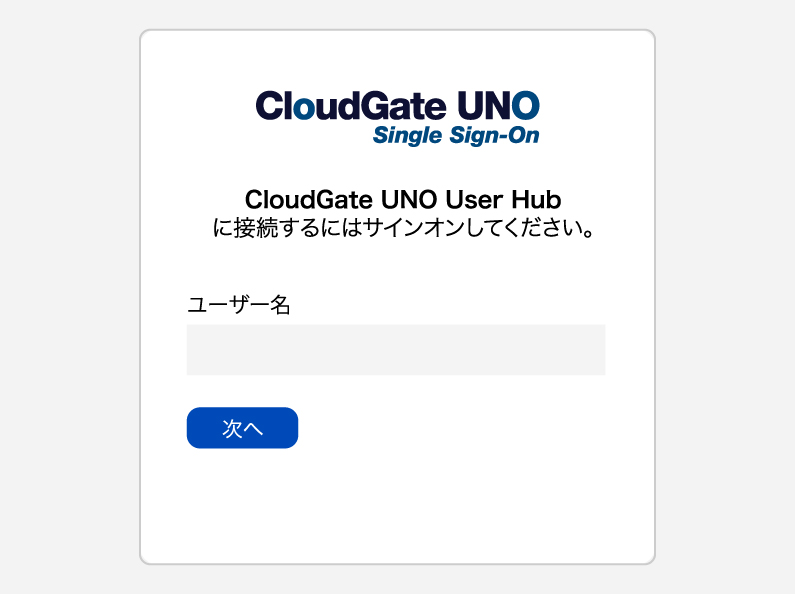
Open the sign-on screen, enter your username, and click "Next."


Select "FIDO2 (Passkey)."

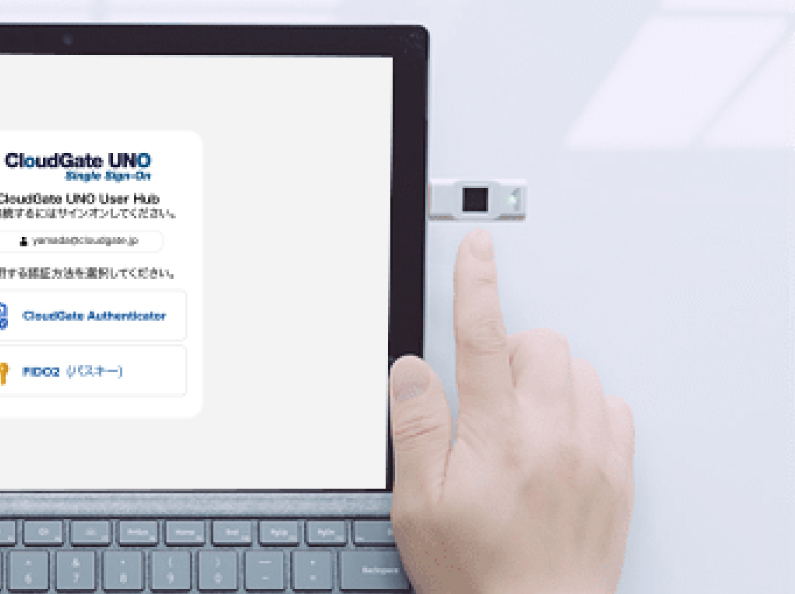
Insert the Security Key into the device and authenticate with PIN + touch or fingerprint.
Note: As this is a FIDO-enabled Security Key, it will be treated as "Passkey Authentication" within CloudGate UNO.
Security Key Services Provided by CloudGate UNO
On July 24, 2024, we proudly launched "YubiKey as a Service," the first subscription-based service in Japan for Yubico's FIDO-enabled Security Key, YubiKey. This service reduces the initial cost of YubiKey deployment, minimizes post-implementation management efforts, and allows you to select the Security Key that best meets your needs from a wide lineup.

Reduced Initial Cost
Being a subscription model, our phishing-resistant MFA solution (YubiKey) can be implemented as an operating expense (OpEx).

Flexibility
During the contract period, you can switch to a different type of YubiKey within the subscription-eligible lineup, even if it differs from the initially deployed type.

Investment in the Future
Protect user system access with a priority on the latest authentication technologies, adapting to business expansion, employee departures, or lost keys.

Effective Implementation
We provide support from security experts, including Customer Success Managers (CSM), for a smooth implementation process.
By combining CloudGate UNO's Single Sign-On with Security Keys, you can apply phishing-resistant authentication even to cloud services that do not natively support passwordless authentication.
Furthermore, you can change authentication methods based on the convenience and confidentiality of the integrated cloud services. For example, you can set different access conditions for email services or attendance management tools, which are frequently accessed from outside the office, versus highly confidential services accessed from within the office. This allows you to build an authentication process that aligns with your corporate security guidelines and actual usage environment, enhancing both convenience and security levels.
Learn more about CloudGate UNO



