Log Reports
Centralize Logs for Enhanced Security
Track and analyze all activity through CloudGate UNO with centralized logs of authentication events and administrator operations. Quickly identify unfamiliar security actions to proactively prevent unauthorized access and mitigate potential damage.

What is a Log?
A log refers to both the act of recording events and information, and the resulting records themselves. In CloudGate UNO specifically, logging involves recording the history and results of the authentication process and the operations performed on the administrator's site.
Centralized management of all history
You can search and check the history of authentication processes performed via CloudGate UNO and the history of operations performed on the administrator’s site. This also minimizes damage from unauthorized access by quickly detecting security-related operations that the user does not remember.
Three points of Authentication log and Operation log

Quickly identify the cause of restricted access

Quickly confirm unfamiliar operations and minimize damage from unauthorized acces

Operation log allows supervision of multiple system administrators
Enhanced Security Monitoring with CloudGate UNO Logs
Authentication Logs
Review detailed records of user login attempts and authentication processes.
Security Detection
Users receives notifications regarding suspicious or unfamiliar security-related changes and activities.
Operation Logs
Track the history of actions performed on the administrator site and system processes.
User operations can be checked
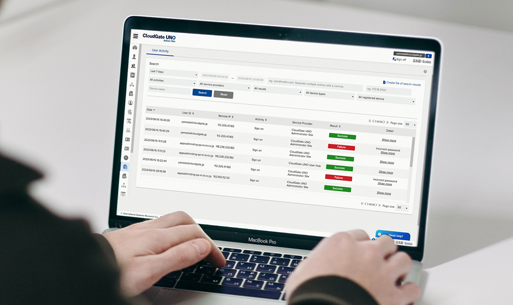
The authentication log is a function that allows you to check the details of activity information such as sign-on, sign-off, and password changes for all users on the administrator site (CloudGate UNO Admin Site). You can search for activities by user and check the reasons for access restrictions, etc.
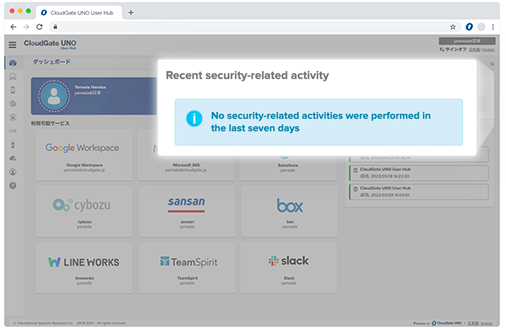
Notifies users about security-related changes
Security detection is a function that notifies users of security-related actions (activities) such as password changes and resets performed by users*. Appears in each user’s user hub and allows users to see activities they don’t know about.
System administrators are encouraged to take appropriate measures for each activity when a user inquires about an activity that they do not recognize.
* Security-related activity for the last 7 days will be notified on the user hub dashboard.
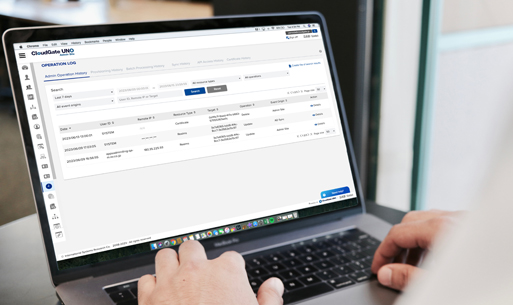
Ability to check history of administrator site operations/program operations
In the operation log, you can check the history of operations on the administrator site (CloudGate UNO Admin Site). It is also possible to check the history of program operations (provisioning, synchronization, API access, certificates) associated with operations.
For companies with many administrators, the chief administrator can supervise other administrators and can be used as an audit log.
Other Features of CloudGate UNO
User Authentication
Enhanced and versatile authentication methods for system administrator to choose from.
Access Control
You can manage the conditions (location/device/time) under which login to the service is allowed.
Active Directory
ID federation and authentication federation by Active Directory federation are possible.
Identity and Access Management (IAM)
It allows centralized management of everything from ID management to lifecycle management such as provisioning.



