Access Control
Flexible Access Control for the Zero Trust Era
CloudGate UNO's flexible access control, built for the Zero Trust era, empowers administrators to easily restrict user access paths by privilege, providing robust protection from threats inside and outside your organization.
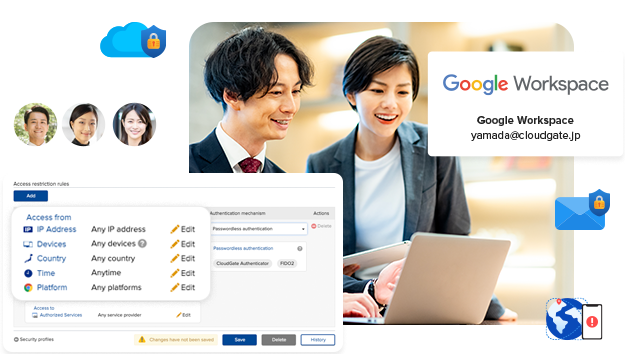
What is Access Control?
Access restriction is a mechanism to limit access routes to linked cloud services. By restricting access in accordance with corporate security rules, important information assets can be protected from threats such as unauthorized access.
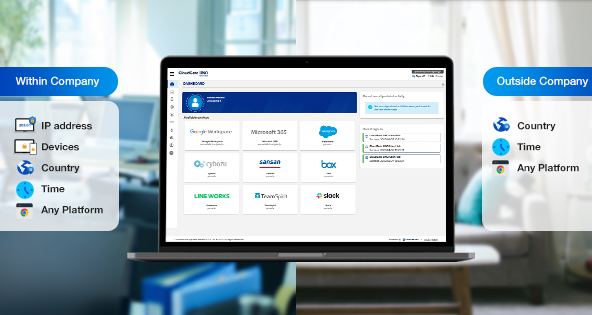
Restrict Access with Zero Trust SSO solution CloudGate UNO
With the spread of cloud services, cyber attacks such as unauthorized access have increased. For future network security, the zero-trust concept of “not trusting all access” in restricting access to linked services is essential.
CloudGate UNO is designed to provide customers with more secure access to cloud services, CloudGate UNO adopts a single sign-on function based on the zero-trust model to enable customers to use cloud services more securely. To achieve secure sign-on, access to cloud services can be restricted by by specifying who, what, when, where, and how to sign on.
CloudGate UNO Identity and Access Management Solution
Flexible access conditions to suit each individual’s working style
As a way to prevent unauthorized access to important corporate information while taking advantage of the convenience of cloud services that can be accessed from anywhere at any time, access restrictions that limit the environments in which you can log in to cloud services are essential.
CloudGate UNO can set multiple access conditions and authentication methods for each service according to the security level and usage environment, realizing flexible access restrictions for the Zero Trust era.
For example:
• Restrict access to inside the company only (IP address restriction)
• Restrict cloud services that can be accessed from outside the company (authorized service restrictions)
• Enable access from outside the company to PCs taken out by employees or departments who often go out (terminal restrictions)
• Allow access only on specific corporate devices (Terminal restriction by certificate CloudGate certificate)
• Temporarily allow access from certain countries, such as when traveling (Access restrictions by country)
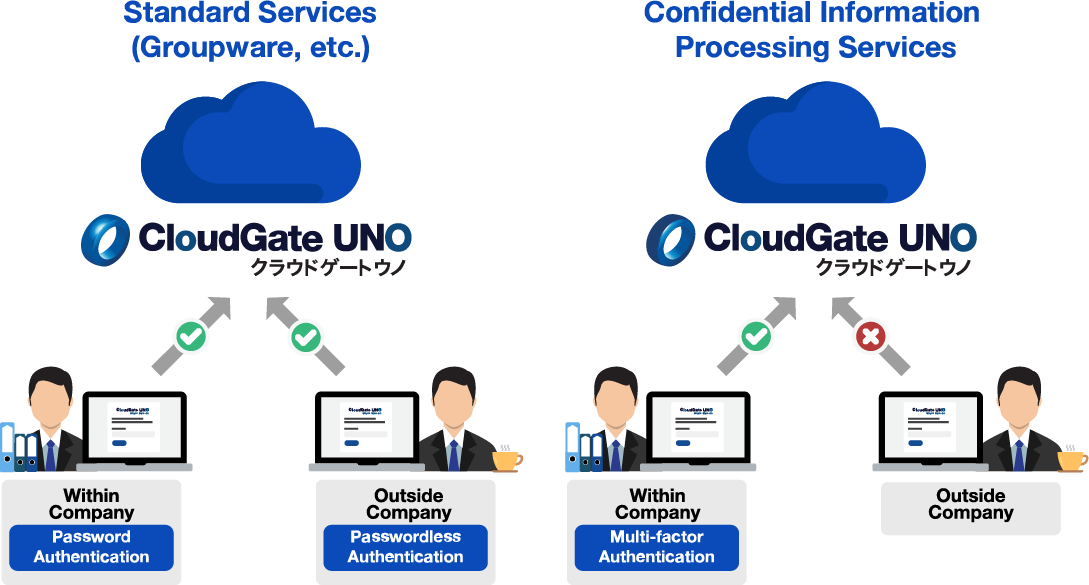
• Use a strong authentication method for identity verification only for cloud services that handle confidential information (Authentication method setting)
By setting a security profile that combines the above access rules for each user, it is possible to achieve flexible access restrictions that match each individual’s work style.
What Access Control Can Solve

Strong Defense Against Cyberattacks
Implement Zero Trust access restrictions to effectively counter increasingly sophisticated cyber threats.

Enhanced Data Security
Achieve stricter management of confidential information with granular security rules tailored to each cloud service.

Secure and Flexible Access
Enable secure remote and diverse working styles by dynamically adapting authentication methods based on work location and context.
Type of Access Controls
Device-based
Allow access only from specific devices
Location-based
Allow access only from specific locations (IP addresses)
Time & country-based
Allow access only for certain time zones and countries
Cloud Service-based
Allow access from outside the company only to specific cloud services.
Enhanced Authentication
Enhanced authentication methods for specific cloud services
Allow access only from specific devices
Device restrictions by browser
Allows access only to terminals (web browsers) that have cookies registered, and limits the terminals that can access. For example, a cookie can be registered on a company-issued device to restrict access from other devices, and similarly, access from personal devices such as employee smartphones can be restricted.
Device restriction by certificate (CloudGate certificate)
By installing a device certificate on the terminal in advance, CloudGate UNO checks whether the accessing terminal has the device certificate and blocks access from the terminal that does not have the device certificate.
Even if your login ID and password are known to a malicious third party, you can prevent unauthorized access from devices that do not have a device certificate.
LLearn More about Digital Certificate Authentication for Secure Access Control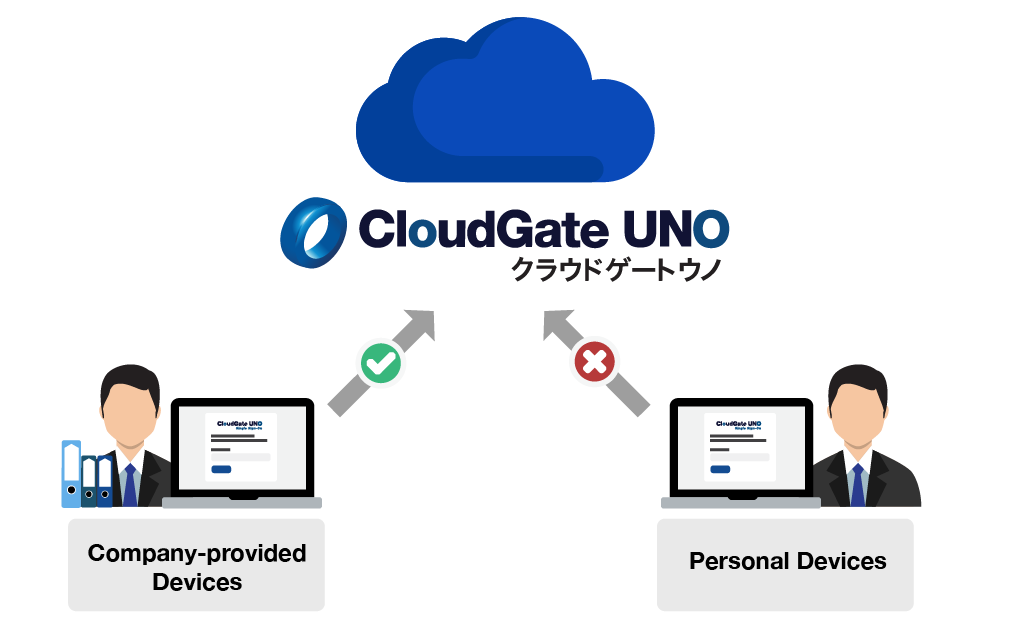
Access restrictions at specific locations (IP addresses)
By registering a global IP address that allows access, you can limit the locations that can be accessed. For example, by registering the global IP address of the office, you can restrict access only from within the office. Also, by registering multiple IP addresses, access from each location is possible even if there are multiple offices.
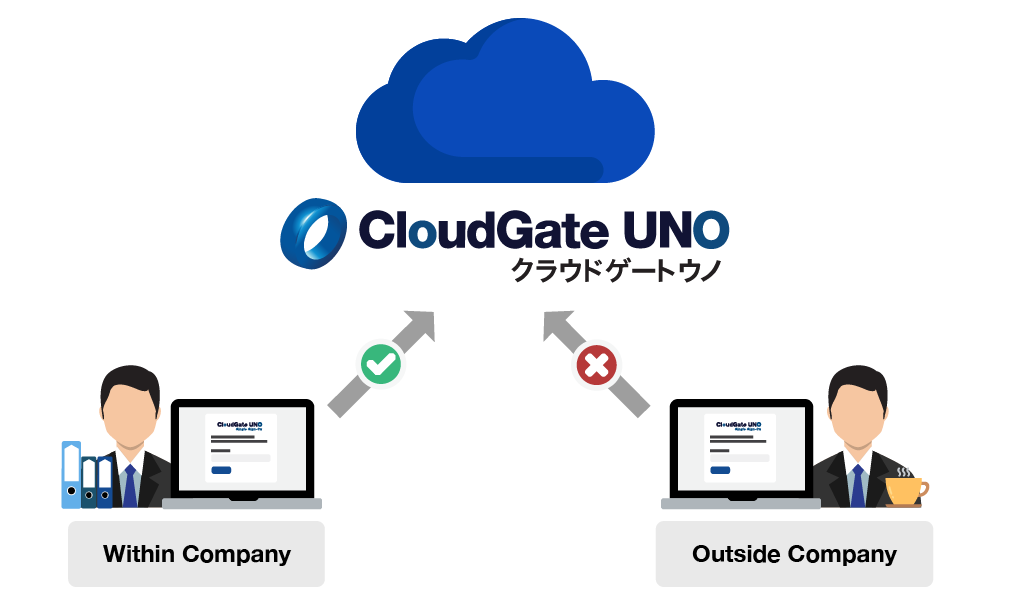
Allow access only for certain time zones and countries
Allow access only to specified days, hours, and countries, and restrict time zones and countries. For example, for users who work fixed hours, such as part-time workers, it is possible to restrict the login time frame for accessing the cloud services.
* “Time restrictions” is a restriction function for login only, and cannot restrict logout.
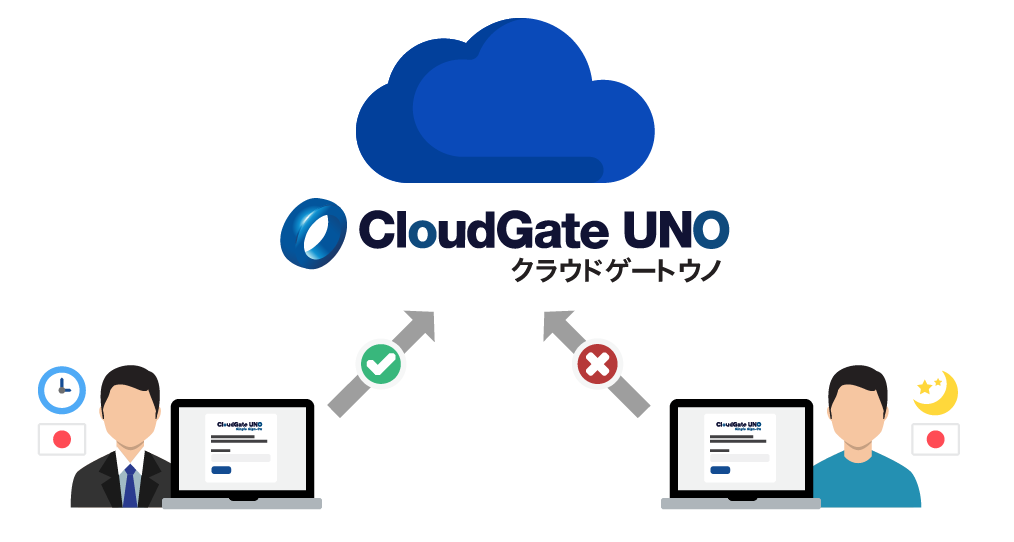
Allow access from outside the company only to specific cloud services.
Cloud services such as groupware allow access from outside the company, but services that handle sensitive information can be restricted to internal access only.
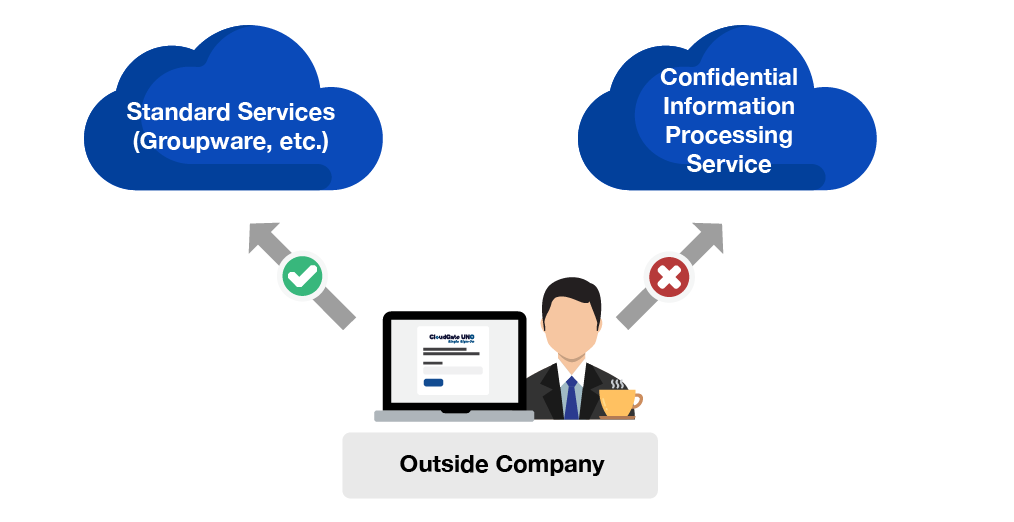
Enhanced authentication methods for specific cloud services
By registering cloud services that allow access (authorization service), you can limit the cloud services that can be accessed. For example, access to cloud services such as groupware can be permitted from outside the office, while access to services that handle confidential information can be limited to within the office.
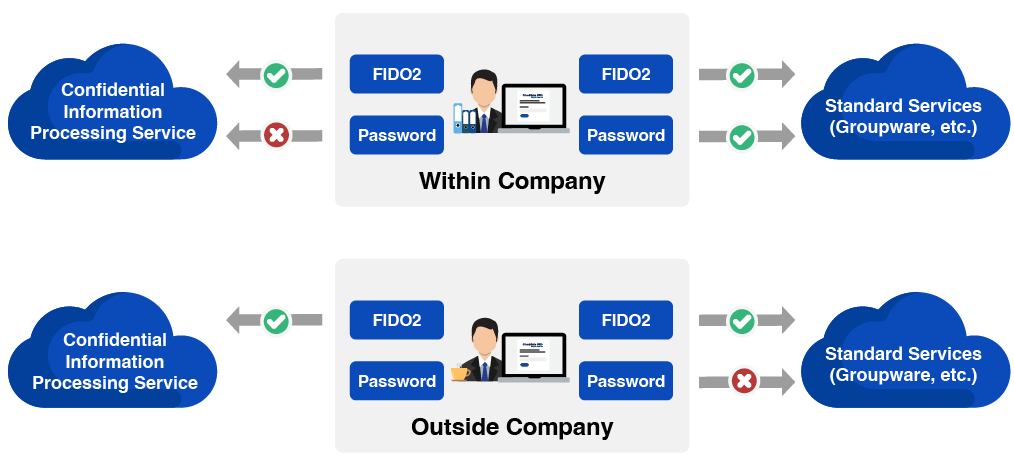
CloudGate UNO Access Restriction Method
Security Profile
Create a profile according to your security settings, can be applied per user.
Access Control
Terminal Limit
- • Access is permitted only from terminals (web browsers) in which cookies are registered, and terminals that can be accessed are restricted.
- • The administrator can limit the number of PCs, smartphones, etc. that can be registered for one user.
IP Address Restrictions
- • Allow access only from the specified global IP address (IP address) and restrict the IP addresses that can be accessed.
- • You can set multiple IP addresses to allow.
Access restrictions by time and country
- Restrict the time zone and country that can be accessed by permitting access only for the specified days, hours, and countries.
Authorized service limit
- • Restrict cloud services that can be accessed by allowing access only from specified cloud services.
- • You can set multiple permitted cloud services.
Identity (Authentication)
- • Authentication is performed according to the matching conditions.
- • Passwordless authentication with FIDO2
- • Biometric authentication (fingerprint authentication, face authentication)
- • Multi-factor authentication by device
- • One-Time Password authentication (OTP)
Access Control Services

Device Restriction by Certificate
Device certificates are easy to use for system administrators and users alike, and provide robust security without compromising the convenience of SSO.

Smart Device Security
Introducing CloudGate UNO’s security features that enable more secure use of smart devices such as smartphones and tablets.
Dedicated Mobile Admin Screen
When you need to urgently unlock a user's account while you're out of the office or after hours, our dedicated mobile admin screen lets you easily resolve account lockouts on the go.
Other Features of CloudGate UNO
User Authentication
Enhanced and versatile authentication methods for system administrator to choose from.
Access Control
You can manage the conditions (location/device/time) under which login to the service is allowed.
Active Directory
ID federation and authentication federation by Active Directory federation are possible.
Identity and Access Management (IAM)
It allows centralized management of everything from ID management to lifecycle management such as provisioning.



